Identity and Access Management
The CybrSec IAM solution utilizes b² Cryptography, a breakthrough innovation for encryption key distribution and management. Unlike PKI, widely used to secure systems today, b² Cryptography reliably authenticates the user to a service, and authenticates the service to the user. Available on all platforms, this new security solution is a game changer.
CybrSec Identity and Access Management (IAM)
CybrSec’s IAM service has been “cyber-hardened” by integrating b² cryptography at the DNA, or foundational, level to protect the identity of users in the cloud.
There is no question that the cloud has rapidly emerged as the computing environment of choice across all industries. However, even with this radical departure from traditional “corporate” computing, a majority of deployments still use the same authentication and access technologies for the cloud, and they are falling short when it comes to risk mitigation. The CybrSec Identity and Access Management service enables the right user to access the right resources at the right time.
In the Know?
In 2017, the number of publicly disclosed data breaches surpassed 2.5 billion records, up 88% from 2016. With data breaches on the rise, CybrSec has taken an extremely secure approach to Identity and Access Management.
Identity and Authentication
By using b² Cryptography, CybrSec provides a distinct tactical advantage in the authentication and identity protection of users in the cloud. As a user is enrolled in the CybrSec IAM service, a CybrSec ID is created and associated with an assigned portable security token based on b² Cryptography.
To authenticate, users must have their assigned token and provide the required factors of authentication. While the authentication process is simple and easy to use, b² authentication is not susceptible to common attacks, such as brute force, phishing, certificate spoofing, SIM swap, man-in-the-middle, and many more.
For centralized authentication across multiple platforms, the CyberSec IAM service supports alternative authentication methods, such as smart cards for Windows/Active Directory and single-sign-on (SSO). These authentication methods are not recommended but serve as a migration pathway to support existing user infrastructure and workflows while b² implementations are considered.
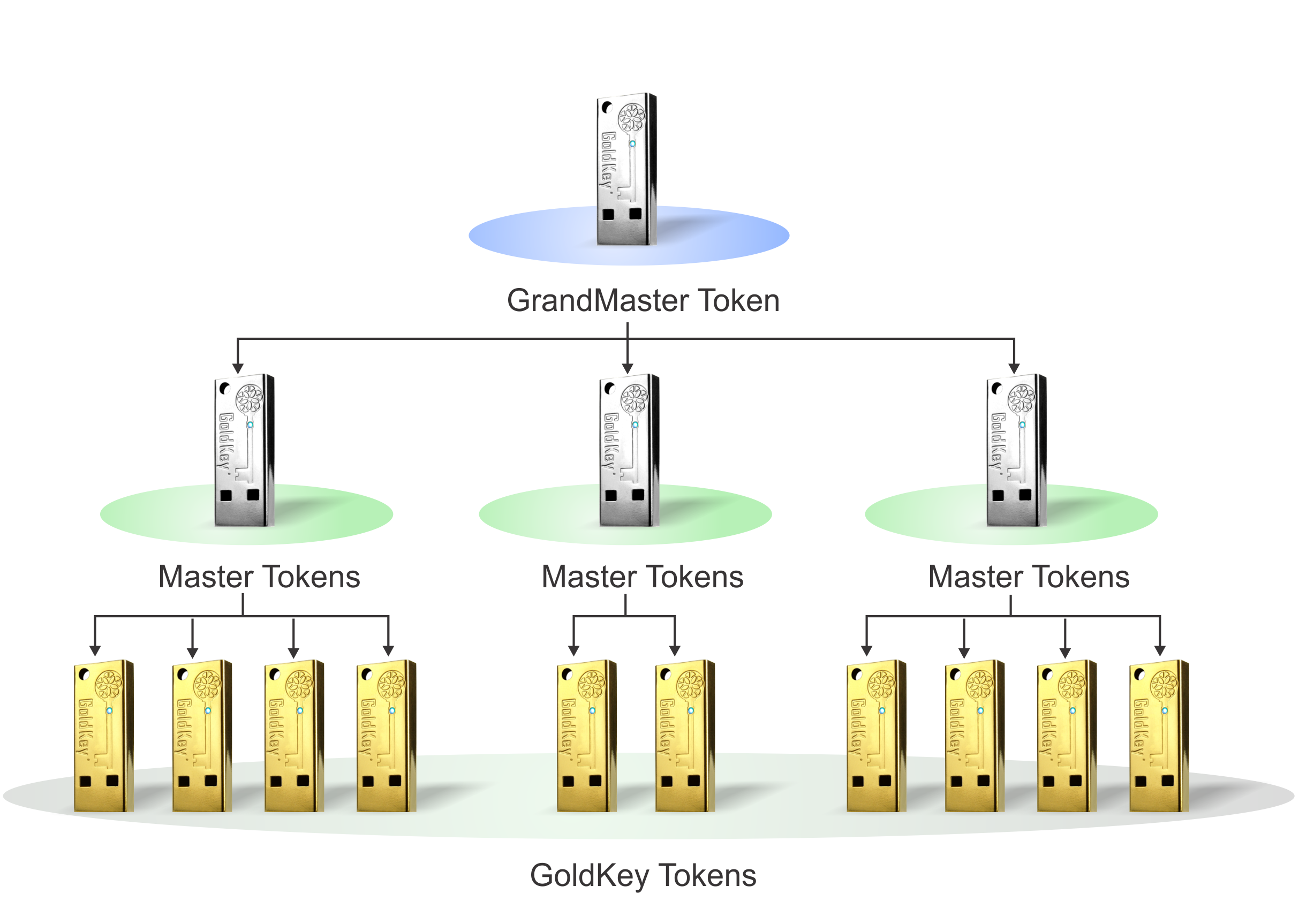
Access Management
CybrSec IAM service utilizes the b² Cryptography hierarchical structure to delegate access privileges from upper management down to each individual user. This hierarchical management defines clear pathways to enforce access policies to secure resources and services. These pathways empower managers to make role-based access decisions at mission speed, without the intervention of IT. In this same way, managers have the ability to revoke access and take back delegated authority.
To secure access to more sensitive data or to enforce compliance policies, administrators can require enhanced authentication. Enhanced authentication requires users to re-authenticate, or provide additional factors of authentication before access is given. The CybrSec IAM solution supports a combination of up to five-factor authentication.
CybrSec provides the most secure Identity and Access Management cloud service today.